The Complete Post-Quantum Cryptography Migration Guide for EDI Systems: Protecting Supply Chain Data from Quantum Threats in 2025
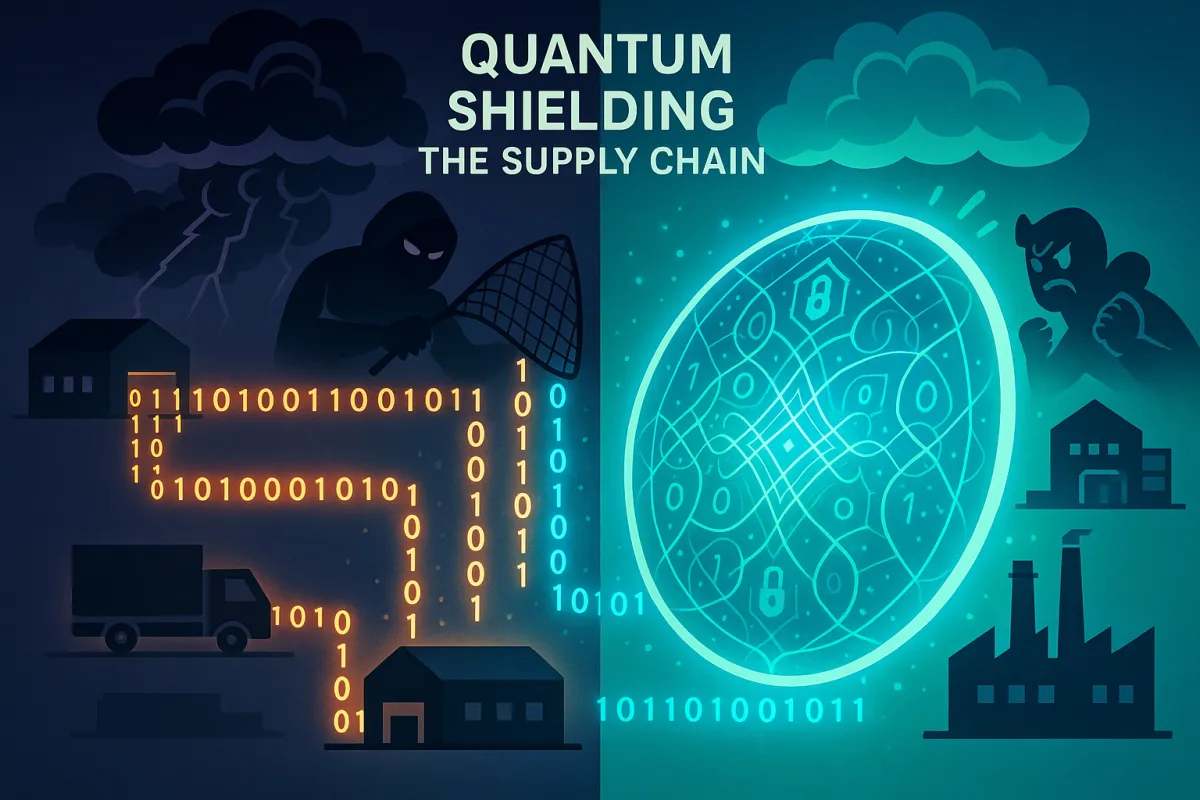
Adversaries are already stealing encrypted data today, storing it securely, and waiting for quantum computers capable of cracking current RSA and elliptic curve encryption. This "harvest now, decrypt later" attack means your EDI transactions from 2025 could be decrypted by 2035. 2025 is an important year - it is probably our last chance to start our migration to post quantum cryptography before we are all undone by cryptographically relevant quantum computers.
The quantum threat timeline has accelerated. Some analysts predicting state actors may have quantum decryption capabilities as early as 2028, while the NSA aims to make all National Security Systems (NSS) quantum-resistant by 2035, aligning with the goals set out in National Security Memorandum-10 (NSM-10). While 2035 is the end goal, the transition begins much sooner. This isn't just a distant government concern - adoption of the new NIST-approved encryption algorithms for post-quantum cryptography for data in transit has started and will slowly climb in 2025, starting first in the especially risk-aware sectors like defense and finance. This will reduce the risk of harvest-now-decrypt-later attacks on confidential data.
Understanding the Quantum Threat to EDI Systems
EDI systems face a dual threat from quantum computing advances. The immediate danger comes from harvest now, decrypt later attacks [that] are already being conducted. Nation-state actors and sophisticated criminals are capturing encrypted EDI transmissions containing supplier contracts, purchase orders, and shipping manifests today. They're storing this data until quantum computers become powerful enough to decrypt it retroactively.
The second threat emerges when quantum computers promises the ability to break RSA, ECC, and other widely-used encryption protocols in seconds — which would otherwise take classical computers millennia. Your EDI system's current 2048-bit RSA keys and elliptic curve algorithms would become useless against a sufficiently powerful quantum computer.
Supply chain data has extended sensitivity periods. Purchase agreements, supplier relationships, and pricing structures in your EDI exchanges often remain confidential for decades. Even if [a quantum computer] is 20 years away, this is relevant because some data that we encrypt today might still require protection 20 years from now. That automotive parts supplier contract you're negotiating via EDI this year? Competitors would love to decrypt those terms in 2040.
The Critical Timeline: Why EDI Systems Need Post-Quantum Migration Now
NIST has set an official deadline for transitioning away from legacy encryption algorithms: by 2030, RSA, ECDSA, EdDSA, DH, and ECDH will be deprecated, and by 2035, they will be completely disallowed. The NSA has been even more aggressive. NSA expects all equipment transitions to be completed by December 31, 2030, well ahead of the 2035 deadline.
For EDI systems specifically, these timelines create urgent pressure. Migrating to PQC is complex and takes years, especially for large enterprises. For example, the shift from SHA-1 to SHA-2 took over 12 years across industries. EDI environments face additional complexity because they involve multiple trading partners, each with their own migration schedules and technical constraints.
Leading EDI providers are already preparing. AWS integrated Kyber into their Key Management Service (KMS) in 2020 as a hybrid post-quantum key exchange option for TLS connections. Other TMS and EDI platforms, including solutions from Cargoson, IBM Sterling, and SPS Commerce, are evaluating similar implementations to support their customers' quantum readiness initiatives.
Post-Quantum Cryptography Algorithms: Evaluating Options for EDI Environments
NIST has standardized three primary post-quantum cryptographic algorithms suitable for different EDI use cases. The National Institute of Standards and Technology (NIST) has selected the CRYSTALS-Kyber Key Encapsulation Mechanism and the CRYSTALS-Dilithium Digital Signature algorithm as primary PQC standards.
ML-KEM (CRYSTALS-Kyber) handles key encapsulation - essentially replacing how your EDI systems establish secure connections. NIST calls its standard, numbered FIPS 203, Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM). Kyber offers three security levels: Kyber-512 (equivalent to AES-128), Kyber-768 (AES-192), and Kyber-1024 (AES-256). We recommend using the Kyber-768 parameter set, which—according to a very conservative analysis—achieves more than 128 bits of security against all known classical and quantum attacks.
ML-DSA (CRYSTALS-Dilithium) provides digital signatures for authenticating EDI messages. This matters for purchase orders, invoices, and shipping notifications where you need to verify the sender's identity. We provide a new encryption technique that relies on the Key Encryption process, namely, Crystals-Kyber, in conjunction with an effective digital signature methodology centered on Lattice-based techniques: Falcon and Crystal-Dilithium.
Both algorithms share computational advantages for EDI implementations. The only operations required for Kyber and Dilithium for all security levels are variants of Keccak, additions/multiplications in Zq for a fixed q, and the NTT (number theoretic transform) for the ring Zq[X]/(X256+1). This means that increasing/decreasing the security level involves virtually no re-implementation of the schemes in software or hardware.
Implementation Challenges: Hardware and Software Constraints in EDI Systems
Post-quantum algorithms create significant implementation hurdles in EDI environments. The primary challenge involves resource consumption. Traditional RSA-2048 keys require 256 bytes, while Kyber-768 public keys need 1,184 bytes - nearly five times larger. Each family presents distinct computational, memory, and energy profiles, making them suitable for different use cases.
Performance impacts vary by EDI system architecture. Hardware accelerators achieve speedups between 3× and 9× over software baseline implementations, even over ones leveraging CPU vector architectures. However, many EDI systems run on legacy hardware without these acceleration capabilities.
Memory constraints pose particular challenges for embedded EDI controllers and edge devices in warehouse management systems. Hardware implementation results show that in terms of hardware efficiency (area-time product), the proposed architecture is 15.8%, 10.7%, and 11.3% more efficient than the state-of-the-art architectures for the three different security levels, but these optimizations require careful architectural planning.
Integration complexity increases when dealing with ERP systems. Experience also shows that in complex systems such as financial networks, upgrading cryptography can take a long time to complete. Your EDI gateway might support post-quantum algorithms, but can your SAP system handle the larger key sizes and modified certificate formats?
Side-channel vulnerabilities represent another concern. NIST paid particular attention to costs in terms of runtime and complexity for implementations that mask runtimes in order to prevent corresponding side-channel attacks (SCA). EDI systems processing sensitive supplier data need protection against timing attacks that could reveal cryptographic keys.
Building a Phased Migration Strategy: The EDI PQC Transition Framework
Successful post-quantum migration requires a structured approach addressing both technical and operational challenges. The framework should begin with comprehensive cryptographic inventory across your EDI infrastructure.
Phase 1: Discovery and Assessment (3-6 months)
Start with conducting a Cryptographic Key Assessment (CKA), which involves reviewing an organization's existing encryption methods, identifying risks and ensuring compliance with security policies. Map every point where cryptography touches your EDI flows - VAN connections, AS2 certificates, SFTP endpoints, database encryption, and API security.
Document partner dependencies meticulously. Your largest supplier might run EDI software from 2015 that can't handle post-quantum algorithms. Create a partner readiness matrix ranking relationships by transaction volume, migration complexity, and business criticality.
Phase 2: Hybrid Implementation (12-18 months)
Deploy hybrid schemes combining classical and post-quantum algorithms. System owners can implement now in order to protect the confidentiality of their data against a quantum capable attacker; namely hybrid implementations that use a combination of pre-quantum and post-quantum schemes. This approach maintains backward compatibility while adding quantum protection.
Leading TMS providers like Cargoson, Cleo, and TrueCommerce are developing hybrid capabilities to support this transition phase. Test these implementations with low-risk trading partners first, gradually expanding to critical relationships.
Phase 3: Full Migration (24-36 months)
Cryptographic agility refers to the ability of a system, platform, application, or enterprise to rapidly adapt its cryptographic mechanisms and algorithms in response to changing threats, technological advances, or vulnerabilities. Build this capability into your migration planning. NIST continues developing additional post-quantum standards, so your systems need flexibility for future algorithm updates.
Establish rollback procedures for each migration step. When a critical supplier can't process your post-quantum secured EDI transactions during Black Friday week, you need the ability to revert quickly without losing trading partner confidence.
Regulatory Compliance and Standards Alignment During PQC Migration
Post-quantum migration intersects with multiple regulatory frameworks affecting supply chain data. GDPR's data protection requirements extend to quantum-safe encryption for EU trading partner information. Healthcare EDI must consider HIPAA implications when patient data flows through quantum-vulnerable systems.
Updating security policies, key management procedures, and internal compliance rules to align with NIST and NSA (CNSA 2.0) recommendations becomes crucial during migration. Your compliance team needs updated data processing agreements with EDI service providers covering post-quantum capabilities.
Industry-specific mandates are emerging. Automotive supply chains face increasing pressure for quantum readiness due to connected vehicle security concerns. Financial services EDI for trade finance must align with banking regulators' quantum risk guidance.
Audit requirements will evolve as post-quantum standards mature. Document your migration decisions, risk assessments, and testing procedures. Auditors will eventually ask why you chose Kyber-768 over Kyber-1024 for specific EDI flows, or how you validated side-channel resistance in your implementations.
Testing and Validation: Ensuring PQC Implementation Security
Post-quantum algorithm implementation introduces new vulnerability classes requiring specialized testing approaches. The cryptography community has already seen a growing interest in understanding potential attack models against quantum-resistant algorithms, such as side-channel and fault injection attacks. In 2025, more experimental research on these threats will occur, aimed at testing, identifying and mitigating potential vulnerabilities.
Side-channel testing becomes particularly important for EDI systems handling sensitive supplier data. Timing analysis attacks could reveal post-quantum private keys by monitoring how long your EDI gateway takes to process different message types. Power analysis attacks on embedded EDI controllers might leak cryptographic material through electromagnetic emissions.
Fault injection testing validates implementation robustness. Can an attacker crash your EDI system by sending malformed post-quantum certificates? How does your system behave when hardware errors corrupt post-quantum signatures during high-volume transaction periods?
Performance validation requires realistic load testing with actual EDI message volumes. The Performance section measures the necessary computational resources required to execute a specific operation, measured in CPU cycles. Test under peak transaction loads - how do post-quantum algorithms perform during month-end invoice processing or seasonal inventory replenishment cycles?
Interoperability testing with trading partners becomes critical. Advanced TMS platforms including Cargoson and other EDI solutions offer testing environments where you can validate post-quantum implementations against different partner system configurations before production deployment.
The quantum threat to EDI systems requires immediate attention, not future planning. The time for enterprise preparation is now. Enterprises that wait until quantum computers reach their full potential to begin planning their transition to quantum-resistant encryption will be too late. Stakeholders must work together to accelerate adoption and ensure a resilient digital future. Start your cryptographic inventory today, engage your critical trading partners in migration planning, and begin testing hybrid post-quantum implementations. Your supply chain's future security depends on the steps you take in 2025.