The Critical EDI Post-Quantum Migration Framework: How to Secure Your Supply Chain Data Exchange Against Quantum Threats Without Breaking Trading Partner Networks in 2025
Your EDI infrastructure sits at the heart of a perfect storm. EU mandates post-quantum cryptography migration by 2026, while adversaries continue harvesting your encrypted EDI transmissions today, banking on quantum computers eventually breaking through your current RSA and ECC protections. Unlike generic enterprise systems, EDI networks present unique challenges: they exchange purchase orders and container tracking data across hundreds of trading partners, many using decades-old systems that weren't designed for cryptographic agility.
The catch? You can't simply flip a switch to quantum-safe algorithms without potentially breaking critical supplier connections that keep your production lines running. This guide provides a strategic framework for protecting your supply chain data exchange against quantum threats while maintaining the trading partner relationships your business depends on.
The Urgent Quantum Threat to EDI Systems
Most supply chain professionals focus on traditional EDI security concerns like data mapping errors or connection failures. Meanwhile, hackers are systematically harvesting encrypted EDI data today, storing it for future decryption when quantum computers arrive - a practice called "harvest now, decrypt later" that puts valuable long-term data like financial records and confidential customer information at immediate risk.
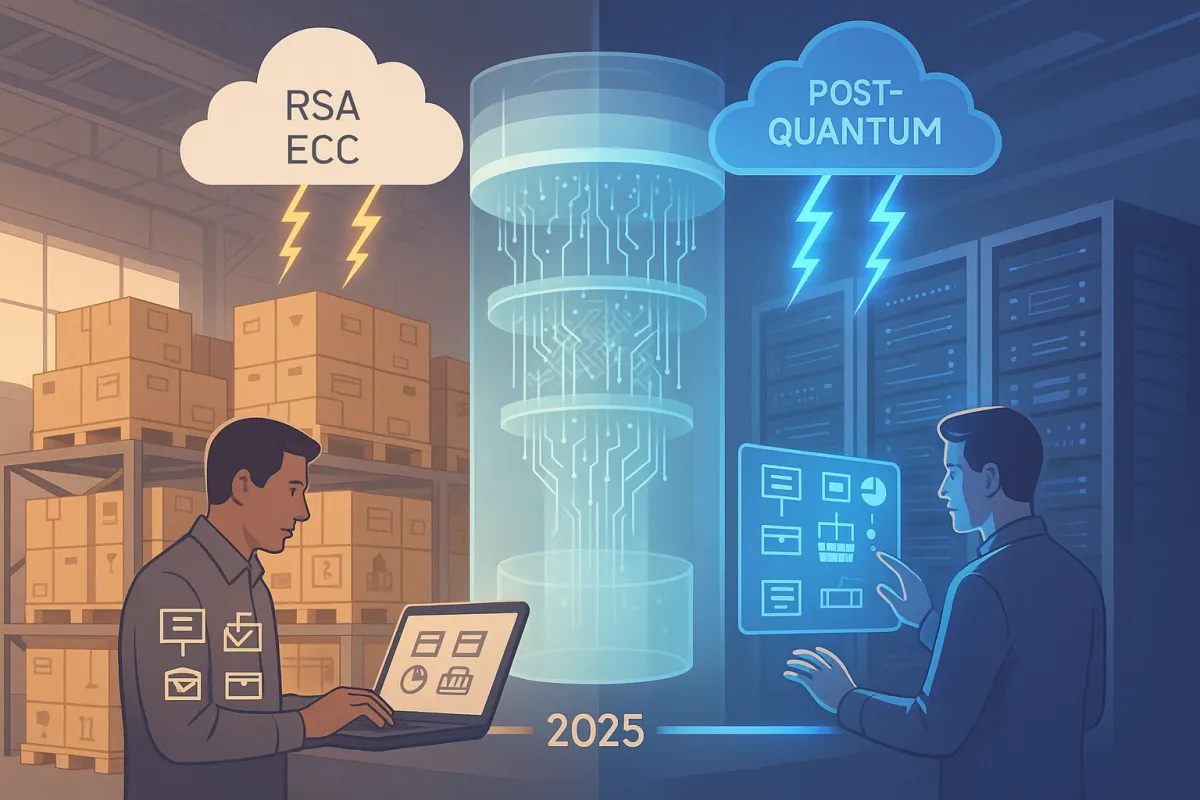
Your EDI systems face particular quantum vulnerabilities because much of the logistics sector's data security today relies on classical public-key cryptography like RSA and elliptic curves. A sufficiently powerful quantum computer running Shor's algorithm could solve these mathematical problems, meaning it could crack RSA/ECC and derive secret keys from public information - making any encrypted supply chain data protected by those algorithms vulnerable.
The timeline has accelerated rapidly. EU Member States must start transitioning to post-quantum cryptography by the end of 2026, while the US follows CNSA 2.0 guidelines with deadlines between 2030 and 2033, and the European Union published their roadmap with 2030 and 2035 deadlines depending on application. For EDI systems supporting TMS vendors like MercuryGate, Descartes, or newer players like Cargoson, this means coordinating quantum-safe connections across your entire ecosystem.
The $7.1 Billion Problem: Why Standard PQC Guidance Fails for EDI
While governments allocate massive budgets for post-quantum transitions, most guidance treats cryptography as a simple algorithm swap. EDI environments present complications that generic advice doesn't address.
Post-quantum algorithms generally require larger key sizes and more complex computations compared to traditional methods, leading to higher processing power and memory requirements, affecting performance especially in resource-constrained environments like IoT devices and real-time systems. For EDI systems processing thousands of transactions daily, these computational overhead increases can impact critical batch processing windows.
The larger key sizes create message size issues. EDI has strict format limitations - EDIFACT and X12 messages have size constraints that larger quantum-safe keys could breach, requiring protocol modifications. Add the challenge of coordinating hundreds of trading partners, each moving at different speeds toward quantum readiness, and you have a migration complexity that standard enterprise crypto guidance simply doesn't address.
EDI providers like SPS Commerce, TrueCommerce, and Cleo must coordinate these transitions carefully. Many enterprises lack the necessary knowledge and expertise to implement PQC solutions effectively, and unlike traditional encryption algorithms standardized for decades, PQC is still evolving with many existing systems not designed to handle post-quantum primitives.
The Complete EDI Post-Quantum Risk Assessment Framework
Start with a cryptographic inventory specifically focused on EDI components. Map every encryption touchpoint: AS2 connections, SFTP transfers, VAN communications, API gateway protections, and certificate-based authentication systems. The most important first step in the PQC transition is understanding your current cryptographic footprint - agencies should begin by conducting a full inventory of systems using vulnerable encryption algorithms, including identifying where encryption is used, the types of protocols in play, and the sensitivity of protected data.
Create a partner vulnerability matrix rating each trading partner's quantum readiness across five dimensions: current encryption methods, system age, IT sophistication, migration timeline commitment, and data sensitivity. This helps prioritize which relationships need immediate attention versus which can follow later waves.
Assess data sensitivity beyond typical classifications. EDI transmissions contain competitive intelligence embedded in order patterns, supplier relationships, and pricing structures. Every piece of encrypted data - from manufacturing specifications to financial details and customer data - could be vulnerable to future quantum decryption, creating cascading risks. Historical EDI data may reveal strategic information worth protecting for decades, not just the typical three-to-five-year encryption lifecycle.
Tools for Discovery
Deploy network scanning tools to identify cryptographic protocols in use across your EDI infrastructure. Tools like Nessus or OpenVAS can discover certificate types and key lengths. For deeper analysis, consider specialized quantum readiness assessment tools that map algorithm usage across your entire technology stack.
The Hybrid Implementation Strategy: Protecting EDI Without Breaking Trading Partners
Pure quantum-resistant deployments remain impractical for complex EDI networks in 2025. Hybrid approaches combining classical and post-quantum algorithms will dominate enterprise implementations - this pragmatic strategy provides defense-in-depth while allowing organizations to maintain operations with current and legacy systems.
Implement NIST's ML-KEM standard alongside existing RSA for key exchange, creating dual-protection that maintains backward compatibility. Research demonstrates fully hybrid TLS protocols that integrate both classical and post-quantum algorithms, combining Curve448 with Crystals-Kyber1024 for hybrid key exchange, and Ed448 with Crystals-Dilithium5 for hybrid digital signatures.
Phase your rollout strategically. Begin with your highest-value, most technically capable partners who can support hybrid implementations. Create connection profiles for different partner readiness levels: quantum-ready partners get full PQC, hybrid-capable partners get dual algorithms, and legacy systems maintain classical encryption with enhanced monitoring.
Solutions providers are adapting their platforms accordingly. While established players like SPS Commerce and TrueCommerce develop their quantum strategies, newer platforms like Cargoson are building crypto-agility into their architecture from the ground up, offering flexible deployment models that can evolve with quantum security standards.
Trading Partner Coordination: The Make-or-Break Success Factor
The technical migration is often easier than managing the human coordination required. Organizations must assess the quantum readiness of their entire partner ecosystem, including developing communication protocols for coordinating cryptographic updates with partners, establishing minimum security requirements for vendors, and potentially providing resources to help smaller partners make the transition.
Draft partner communication templates explaining the quantum threat in business terms. Most trading partners won't understand cryptographic details, but they will respond to compliance deadlines and security breach risks. Include specific timelines, testing procedures, and fallback plans for connections that fail during migration.
Establish quantum readiness as an EDI onboarding requirement. New trading partners should demonstrate crypto-agility capabilities before integration. This prevents accumulating additional technical debt as you work to modernize existing relationships.
Create testing protocols that validate both classical and quantum-safe connections work properly. Design rollback procedures for when migrations fail - because they will. Critical supply chain connections can't afford extended downtime while debugging quantum cryptography implementations.
Performance and Cost Impact Analysis: Real Numbers for Budget Planning
Post-quantum algorithms impose measurable performance overhead that EDI systems must accommodate. ML-KEM key generation takes 2-3 times longer than RSA-2048, while ML-DSA signatures are significantly larger than ECDSA equivalents. For high-volume EDI processors handling 10,000+ transactions daily, this translates to extended batch processing windows and increased bandwidth requirements.
Key size increases affect more than performance. EDIFACT message segments have length limitations that larger quantum-safe certificates might exceed. Budget for message format modifications and testing across your trading partner network. Some legacy VANs may require infrastructure upgrades to handle larger message sizes.
Calculate total cost of ownership including partner coordination. Internal system upgrades typically cost $50,000-200,000 for mid-sized EDI environments, but supporting partner migrations can triple those figures when you factor in testing resources, extended parallel operations, and potential connection failures requiring manual intervention.
Compare these costs against quantum attack impacts. Organizations demonstrating quantum-safe crypto roadmaps enhance trust and reputational assurance, while ignoring the issue could mean data you thought secure might be decrypted by adversaries in a decade, with disastrous consequences for privacy and trust. A single major EDI data breach exposing customer order patterns or supplier relationships could cost millions in competitive damage and regulatory penalties.
Future-Proofing Your EDI Investment: Beyond 2030 Compliance
Build crypto-agility into your EDI architecture rather than treating quantum resistance as a one-time migration. Networking teams should begin evaluating hardware and software platforms that support cryptographic agility - the ability to swap algorithms without architectural redesign is critical as algorithms will now require ongoing management.
Design for algorithm evolution. In March 2025, Hamming Quasi-Cyclic (HQC) was selected as a Key Encapsulation Mechanism for standardization among the fourth-round finalists, complementing the previously standardized CRYSTALS-Kyber KEM. Your EDI systems need flexibility to adopt future algorithm updates without major infrastructure overhauls.
Establish continuous cryptographic monitoring. Deploy tools that track algorithm usage across your EDI network and alert you to deprecated methods before they become vulnerabilities. This prevents the reactive scrambles that characterize most cryptographic upgrades.
Forward-thinking organizations are choosing platforms designed for this evolution. While legacy EDI providers focus on maintaining existing systems, newer solutions like Cargoson are architecting quantum-ready infrastructures that can adapt as post-quantum standards mature, offering the flexibility needed for long-term supply chain security.
The quantum threat to EDI systems isn't theoretical - it's already changing how adversaries collect your encrypted data. Start your risk assessment now, engage your critical trading partners in migration planning, and choose technology solutions that can evolve with the rapidly advancing quantum security landscape. Your supply chain data exchange depends on it.